Restrict External Access
Fine grained access to ICA features can be controlled based on where a user is accessing ICA from. This can be useful to grant different levels of access to operators depending if they are accessing from your local network or from the public internet.
System Setup
If an HTTP request contains a request header X-Patriot-External then Patriot will treat that connection as "External Access".
It is recommended to add the X-Patriot-External header for any requests which originate from outside your internal network. Detecting if a request originates from outside your internal network depends on your particular IT infrastructure.
IIS Configuration
If using IIS reverse proxy configuration to forward ICA requests to patriot then read Microsoft's documentation on conditionally adding HTTP request headers.
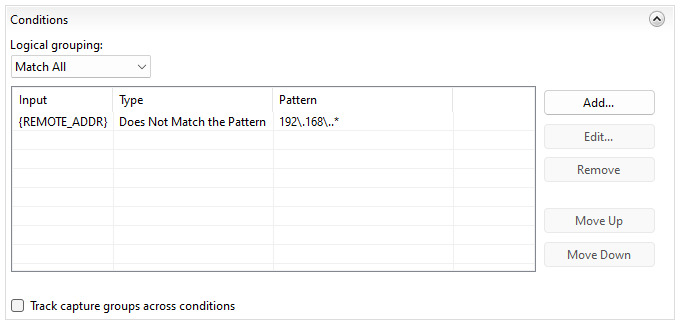
An example condition to detect external access (any IP Address not matching the pattern 192.168.*) is the following:
<conditions logicalGrouping="MatchAll" trackAllCaptures="false">
<add input="{REMOTE_ADDR}" pattern="192\.168\..*" negate="true" />
</conditions>
Security Group Setup
See here for instructions on configuring which Security Groups can/cannot be accessed via "External Access".